Maximizing Company Security: The Ultimate Overview to Electronic Security Solutions
In the busy and ever-evolving landscape of business safety and security, the dependence on electronic security remedies has actually come to be extremely important for safeguarding valuable possessions, private info, and maintaining operational continuity. As dangers to businesses continue to grow in intricacy and regularity, the requirement for an extensive and durable protection strategy can not be underrated. In this guide to electronic safety services, we will certainly check out the latest patterns, advanced modern technologies, and ideal practices to strengthen your service against prospective threats and vulnerabilities. Remain ahead of the contour and make sure the security of your business with our extensive assessment of electronic security services.
Value of Electronic Protection Solutions
When taking into consideration the protection of possessions and sensitive info, the importance of electronic security solutions can not be overstated. In today's interconnected world, where cyber dangers are constantly evolving and coming to be extra innovative, organizations have to focus on applying durable electronic safety steps to protect their information and procedures. Electronic security services include a large variety of innovations and techniques made to resist unauthorized gain access to, data breaches, malware, and other cyber dangers.
One of the essential advantages of digital protection options is their ability to supply real-time surveillance and threat detection. BQT Solutions. Through devices like intrusion discovery systems, firewall programs, and safety and security information and event monitoring (SIEM) systems, organizations can proactively determine and reply to safety events before they escalate into major breaches. In addition, digital safety solutions assist ensure compliance with sector laws and standards, protecting companies from possible legal and monetary effects
Sorts Of Electronic Safety And Security Solutions
Provided the essential significance of digital safety and security solutions in protecting companies versus cyber threats, it is essential to check out the different kinds of digital safety and security systems available to boost protection and durability. One of the most typical kinds of digital security systems is the firewall, which acts as an obstacle between a firm's inner network and external networks, filtering system out potentially unsafe data. By using a mix of these digital safety systems, businesses can develop a robust defense versus various safety and security hazards.
Implementing Access Control Procedures
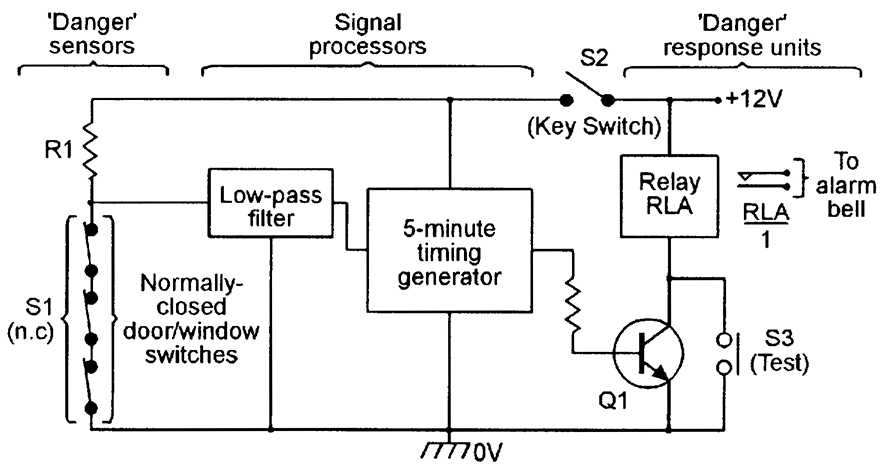
Additionally, accessibility control measures can be incorporated with surveillance systems to keep track of and videotape individuals' activities within protected locations. This assimilation enhances safety and security by offering an extensive review of that is accessing particular locations at any type of provided view it time. Moreover, gain access to control systems can be configured to limit gain access to based on time, area, or private qualifications, enabling companies to customize protection protocols according to their details needs.
Cybersecurity Ideal Practices
To improve total protection pose, implementing durable cybersecurity finest practices is critical in guarding digital possessions and data stability. Performing routine security audits and evaluations aids determine weak points and areas for enhancement.
Establishing a comprehensive case action plan makes it possible for swift and effective actions to security breaches, reducing prospective damage. Carrying out gain access to controls based on the concept of least advantage limits the direct exposure of essential systems and info to only those that need it for their functions. By incorporating these finest practices into cybersecurity approaches, organizations can strengthen their defenses against webpage evolving cyber threats.
Surveillance and Monitoring Solutions

Video monitoring click here to read services provide remote surveillance abilities, permitting accredited employees to watch on the properties even when off-site. Furthermore, advanced functions like motion detection, facial acknowledgment, and permit plate recognition improve the overall safety stance of the company. Incorporating surveillance systems with security system and accessibility control even more enhances the safety and security facilities, making it possible for a positive action to possible security breaches.
Conclusion
In verdict, digital safety and security solutions are essential for optimizing service protection. It is important to spend in the right digital protection systems to make certain the security and security of the organization.